Foto A: A Real wireless hotspot login page

Foto B: A Fake wireless hotspot login page

Video 1: Fake AP in action
Want to turn your normal and innocent looking wifi adapter into a fake access point and able to do EXACTLY as above video? Just follow the 3 simple step.
Requirement:
-------------------
#1. Backtrack4
#2. Your pc must already be connected to internet service via item #4
#3. 1 usb wifi adapter (mine is ralink, yours might differ). This wifi adapter will be transformed into a fake access point where all the victims will be connected to. Here is where DNS poisoning, 'Secure site' SSL sniffing, email and instant messaging monitoring is being done. You will be able to see exactly what the victim saw on their pc screen, remotely.
#4. 1 usb or internal wifi adapter (mine is centrino, yours might differ). This wifi adapter will be connected to the internet (item #2) and forward all internet traffic to item #3.
#5. fakeap.sh and dhcpd script software
Step 1. Download fakeap.sh and dhcpd.conf onto the Bt4 desktop. This is a trial version.
Step 2. Open konsole and type in 'chmod {leave a space} +x {leave a space} /root/fakeap.sh' then
Step 3. type in '/root/fakeap.sh' and follow instruction as per Picture A to G below.
*Key in all command without the quote notation.
Picture A: Download 'fakeap.sh' and 'dhcpd.conf' onto bt4 desktop

Picture B: Execute 'fakeap.sh' (trial version) script

Picture C: Unplug wifi adapter to be used as fakeap (mine is 'ralink', yours might differ)
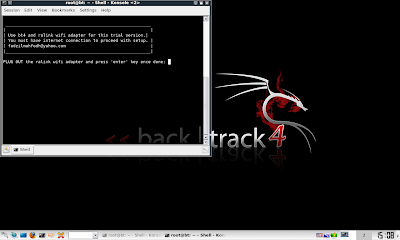
Picture D: Specify interface for internet connection (mine is 'eth1', yours might differ)
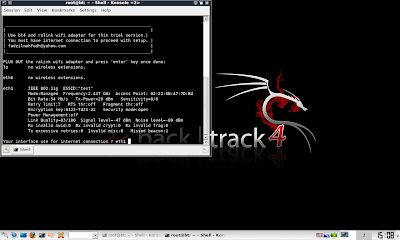
Picture E: Specify IP gateway (mine is '200.70.1.1', yours might differ)
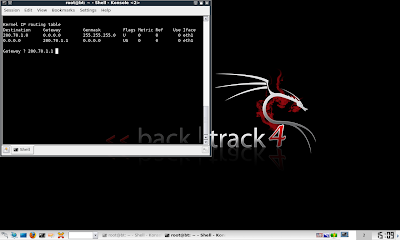
Picture F: Configure 'dhcpd.conf' and plugin wifi adapter to be used as fakeap
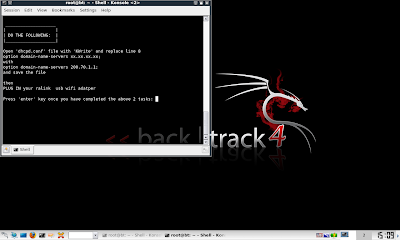
Picture G: 'fakeap' wifi network is now successfully launched.
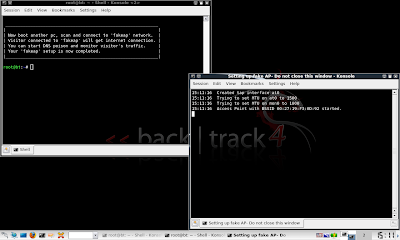
Your wifi adapter is now turned into a fake access point. Your 'fakeap' ssid will be visible by other pc in the vicinity. Unsuspecting visitors who connected to your 'fakeap' will be able to surf the internet as normal, just like what you saw in above video.
We will then do a DOS attack to block all other real ap's broadcast signal so that surfers in the vicinity can only connect to our network. Mid way into their individual internet session (via our fakeap) the script will pop-up an alert message that says "Network disconnected. Re enter WPA key to establish connection." and then prompt a login box asking for WPA key, or popup what ever fake login page you desire. Once victim fall into this fake web page, they will unable to escape from it and entrapped in a loop cycle.

With fakeap.sh (full version) script you will also have additional option to remotely monitor visitor's traffic and inject DNS poison to their internet session to divert them to a fake login web page, if you wish. This attack is only limited by your imagination.
Some people might say this method is more like 'social engineering' than macho 'hacking'. Well, call it what ever you want, to me, the end justified the mean. If i can get 50% success rate using this method, i am a happy man. BTW, what is the success rate if you use pure brute force ? Well, not that good if you ask me.
HOW TO GET FAKEAP FULL VERSION
==============================
You can get your personalized fakeap full version code by sending email to us using the following format (click to see the request code).